Cybersecurity Predictions 2025 – How to Prepare
I’ve been monitoring the cybersecurity space for more than two decades, but cyber threats are evolving at a pace I’ve never seen before. As technology evolves and the use cases…
Most popular
Your Custom GPT: Creating a Personal Brand Adviser
Welcome to the first edition of the UpLevel! Newsletter. I s…
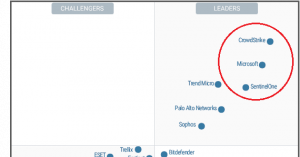
Win at Positioning in 2024: How Cybersecurity Leaders Differentiate
In the ever-evolving landscape of cybersecurity, differentia…
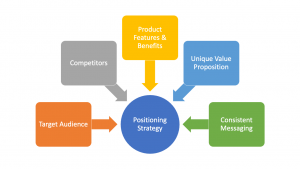
Positioning strategy: How to drive growth in 2024
The product positioning strategy is the cornerstone of any e…
Latest articles
Failing Forward – How to turn Mistake into Great Success
In both business and life, failure is often seen as somethin…
How to Hire a Stellar Product Marketing Manager
On many occasions, I’ve been asked how to find and hire a gr…
Marie Forleo – A Life Coach You Need To Know
Marie Forleo is a name synonymous with entrepreneurial succe…
Pat Flynn – From Architect to Successful Digital Entrepreneur
If you’re into passive income, you have to know Pat Flynn. H…
How Justin Welsh Built a Successful Solopreneur Business
“Don’t you know who Justin Welsh is?” a fo…
How to Effectively Expand Into a New Customer Segment
You can grow so much by focusing on a single customer segmen…