Online Privacy – A Quick Guide To Data Protection Regulations
We live in an era where digital footprints are as significant as a physical presence. Understanding how to protect personal and business data and knowing your rights is more important…
Most popular
Your Custom GPT: Creating a Personal Brand Adviser
Welcome to the first edition of the UpLevel! Newsletter. I s…
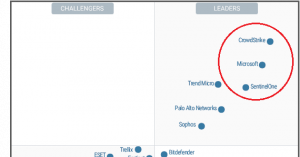
Win at Positioning in 2024: How Cybersecurity Leaders Differentiate
In the ever-evolving landscape of cybersecurity, differentia…
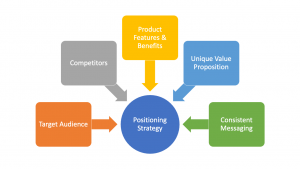
Positioning strategy: How to drive growth in 2024
The product positioning strategy is the cornerstone of any e…
Latest articles
How to Manage the Threats to Your Online Privacy
Have you ever noticed ads for items you’ve just searched for…
How To Close the Strategy Implementation Gap
Over the years, I’ve had my fair share of strategy dra…
Cybersecurity for Small Businesses – The Complete Guide
As a small business owner, you’re in a nonstop whirlwi…
12 Cybersecurity Tips For Small Businesses On A Budget
Many small business owners understandably fear that robust c…
Small Business Cybersecurity How To – Six Easy Steps
Over 70% of US small business owners reported a cyber-attack…
How to Transform Product Marketing with AI
Over the past year, I designed a new go-to-market strategy f…